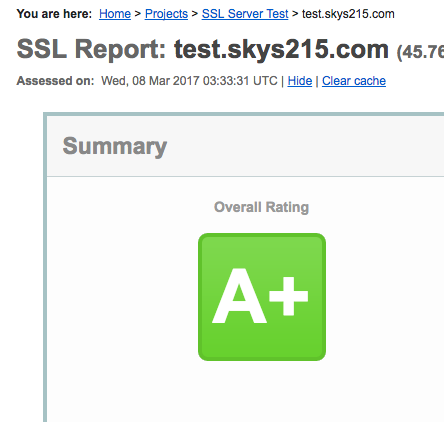
用startssl生成的证书配置nginx的https
- 生成rsa密钥对,
openssl genrsa -aes256 -out my-private-encrypted.key 2048 openssl rsa -in my-private-encrypted.key -out my-private-decrypted.key(建议chmod 600 my-private-decrypted.key)openssl req -new -sha256 -key my-private-decrypted.key -out mydomain.com.csr- 粘贴csr到startssl
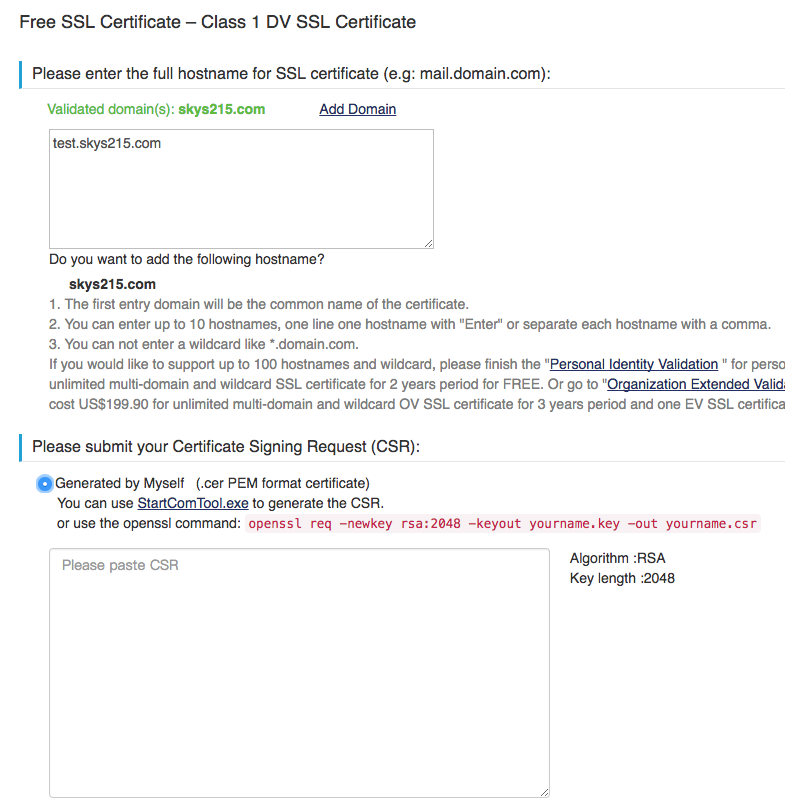
- 然后下载文件,并上传到服务器中。
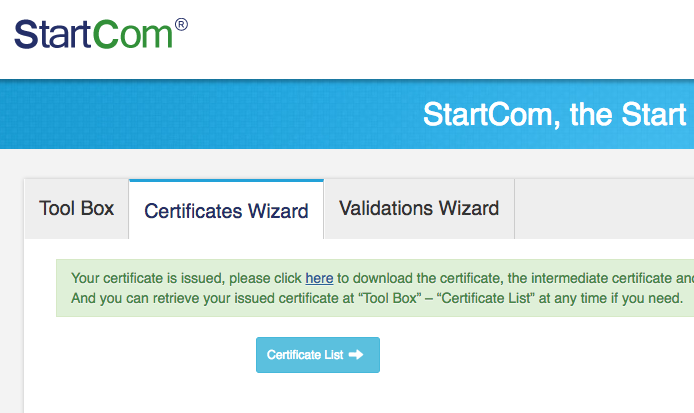
- 在服务器上,刚刚上传文件的地方,下载sub.class1.server.sha2.ca.pem
wget http://plamenatv.free.bg/up.html - 把两个文件合并到一起(不知道为什么要这样做,大概是为了方便引用?)
sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 2048- 修改nginx配置文件
server {
listen 80;
listen [::]:80;
server_name test.skys215.com;
return 301 https://$host$request_uri;
}
server{
listen 443 ssl;
server_name test.skys215.com;
ssl on;
ssl_certificate /path/to/unified.crt;
ssl_certificate_key /path/to/my-private-decrypted.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_dhparam /etc/ssl/certs/dhparam.pem;
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA';
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:50m;
ssl_stapling on;
ssl_stapling_verify on;
add_header Strict-Transport-Security max-age=15768000;
root /var/www/test;
index index.html;
location / {
try_files $uri $uri/ =404;
}
}如果结果是A+那就可以了~
但是,starcom签发的证书已经被chrome和firefox标为不受信任的证书提供商。用以上浏览器打开会显示为不安全。